Balancing external communication in Microsoft Teams is a delicate dance, isn’t it? On one hand, we want to enable collaboration with partners, vendors, and customers. On the other hand, we need to protect our organization from risky domains, unwanted spam, and flat-out malicious actors trying to get in.
That’s why this new update from Microsoft is such a relief. Teams is now integrating with Microsoft Defender for Office 365’s Tenant Allow/Block List (TABL). This is one of those updates that instantly makes security admins breathe a sigh of relief.
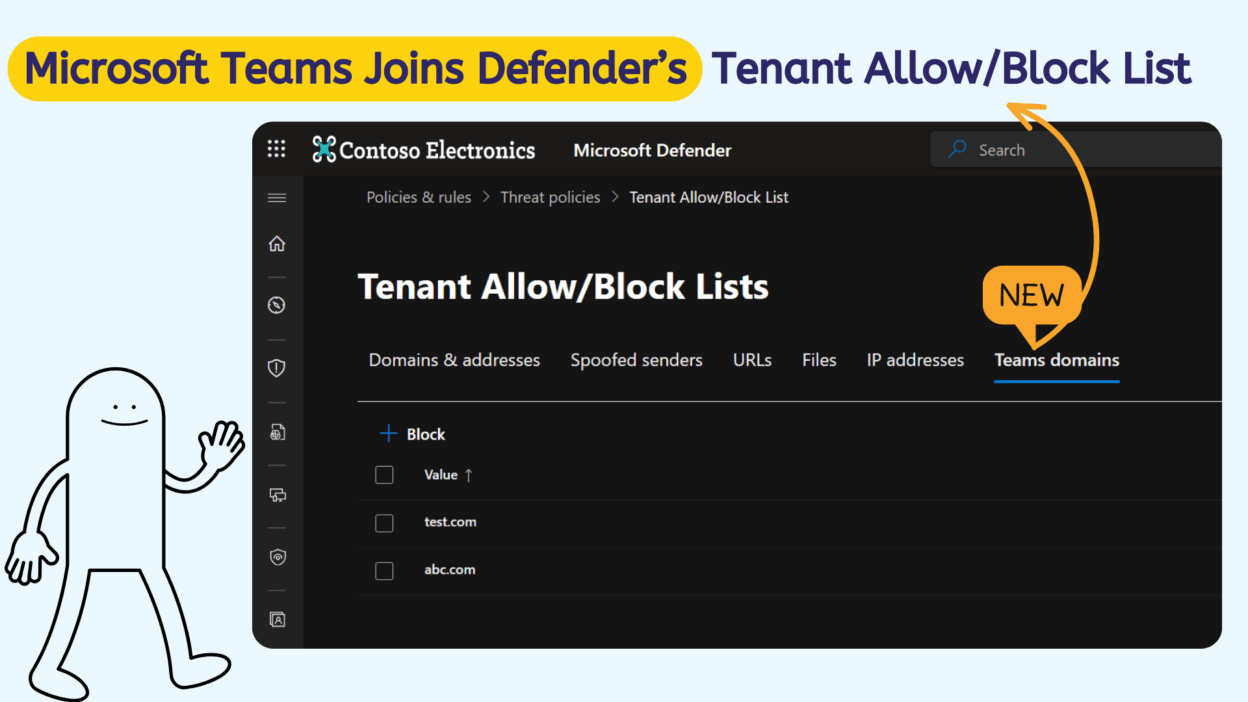
I know, “Tenant Allow/Block List” sounds a bit like a mouthful of tech jargon, but the idea is simple: security admins can now centrally manage blocked external domains in Teams, directly from one central, easy-to-use place—the Microsoft Defender portal.
From late August through October 2025, Microsoft is rolling this feature out, if you’re already using the Tenant Allow/Block List in Defender for Office 365 to secure things like email and other workloads, this is a very natural extension.
The Microsoft Teams Integration with Microsoft Defender for Office 365
Before now, Teams admins had to handle external domain settings from within the Teams admin center alone. That wasn’t bad, but it came with limitations. Security admins, those who are usually responsible for monitoring risky domains across Microsoft 365, didn’t have direct controls over Teams.
This often created a siloed setup. For example, a security admin could block a domain in Exchange Online or SharePoint, but in Teams, that same domain might still sneak through chats, meetings, or channel conversations.
See the problem?
But for the first time, security teams can centrally manage blocked external domains for Teams directly from the Defender portal, without constantly switching configurations across different admin centers.
If you’ve ever had to chase down rogue external chats in Teams or struggled with scattered security settings, this one’s for you. With Teams domain blocking now tied into the Tenant Allow/Block List (TABL) in Microsoft Defender, everything comes together under one roof. In other words, one central list that spans across Microsoft 365 workloads, email, files, and now Teams.
Instead of piecemeal controls, organizations finally get a unified way to stop unwanted domains across email, files, and now Teams conversations.
How to Enable Teams and Microsoft Defender Integration
First, you need to make sure your organization has the right licenses. This feature is available to customers with Microsoft Defender for Office 365 Plan 1 or Plan 2 and, of course, Microsoft Teams. If you’ve got those, you’re all set to move forward.
Next comes a bit of coordination between your Teams admin and your security admin. The Teams admin needs to enable a specific setting in the Teams admin center before security teams can take over. Here’s the step-by-step checklist:
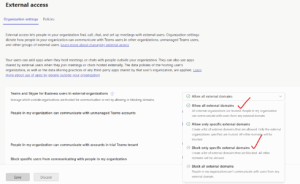
1. First, review your external access settings in Teams:
- Go to the Teams admin center.
- Ensure that external access is set to either:
- Block only specific external domains or
- Allow all external domains.
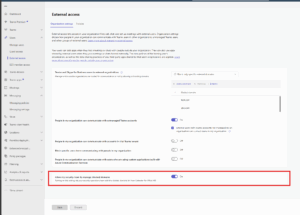
2. If the above is done as expected, then proceed to enable the Security Team Toggle.
- In the Teams admin center, go to ‘External Access’, turn on the setting: “Allow my security team to manage blocked domains.”
- This is off by default. You’ll need to turn it on to let your Defender admins take over.
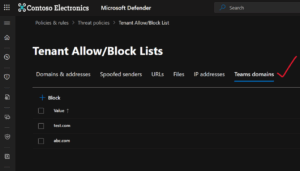
Once that toggle is on, your security team can get to work right from the Microsoft Defender portal. It’s a small change in process that leads to a massive improvement in security and efficiency. In fact, security admins will see a dedicated tab in Defender where they can maintain the Teams blocked domains list alongside other Microsoft 365 services.
I can hear some of you asking, “What about existing federation rules?”. Good question, this update doesn’t overwrite or change your existing federation configurations in Teams. If you already blocked or allowed certain domains through the Teams admin center, those settings stay intact.
TABL integration simply layers centralized controls from Defender.
Key Capabilities for Security Admins
Once Teams admins grant them permission, here’s what security teams can do:
- Unified Domain Blocking
- Instead of having one list for email and another for Teams, security admins can now manage everything in one place: the Microsoft Defender portal.
- Block a malicious domain in Defender, it can be blocked in Teams too.
- Communication Control
- Once a domain is blocked, users from that domain can’t join your Teams chats, channels, meetings, or calls.
- Automatic Clean-Up
- This is my favorite part: Teams will automatically delete existing communications from users in blocked domains. That means you’re not just stopping future risks, you’re cleaning up past exposure too.
One more thing: you can configure up to 4,000 blocked domains for Teams. That’s a pretty generous and should cover the needs of most organizations without hitting a ceiling too soon.
Compliance and Reporting Perks
If you spend your days thinking about audits, regulations, and evidence trails, this is the part you’ll appreciate most.
- With the Teams and Defender integration, every single action—whether it’s blocking, unblocking, or deleting a domain is automatically audited. These audit trails aren’t hidden away either; you can access them through Microsoft Defender or Microsoft Purview, depending on how your organization prefers to monitor compliance.
- These logs give you evidence for regulators and auditors. You can prove you’re not just setting policies—you’re enforcing them.
- On top of that, Entra ID group membership controls make role-based access crystal clear. Only the right admins, assigned through Entra ID, can manage blocked domains. This reduces the risk of accidental changes, keeps responsibilities well-defined, and strengthens your governance posture.
We all know Teams has exploded as a collaboration platform, but with that growth comes new risks. To me, this feels like Microsoft finally connecting the dots between productivity (Teams) and security (Defender for Office 365). Instead of scattered admin efforts, you now get one unified defense strategy that spans collaboration and communication tools.
And while the rollout will continue through early October 2025 (with timelines that may shift slightly), it’s worth preparing now. Check your external access settings and enable that toggle in the Teams admin center if available.
👉 So, what do you think? Will your org make use of this integration from day one? Or are you waiting to see how it fits with your current Teams policies? Either way, I’d love to hear how you’re planning to leverage it!