Microsoft is retiring the legacy policies for multifactor authentication (MFA) and self-service password reset (SSPR). Starting September 30, 2025, you will no longer be able to manage authentication methods in those blades. All management must be done through the Authentication methods policy in Microsoft Entra ID.
This guide walks you through how to migrate, what to watch out for, and how to finish the move without disruption.
Quick Summary (what you must know)
- The Authentication methods policy is now the single place to manage all MFA and SSPR methods.
- The retirement affects tenant-wide legacy MFA and SSPR settings.
- The migration can be done automatically through a wizard or manually for more control.
- The migration is reversible while it is in progress, so you can roll back if something goes wrong.
- The migration must be performed by someone with the Authentication Policy Administrator role or equivalent.
Locations to check in the portal:
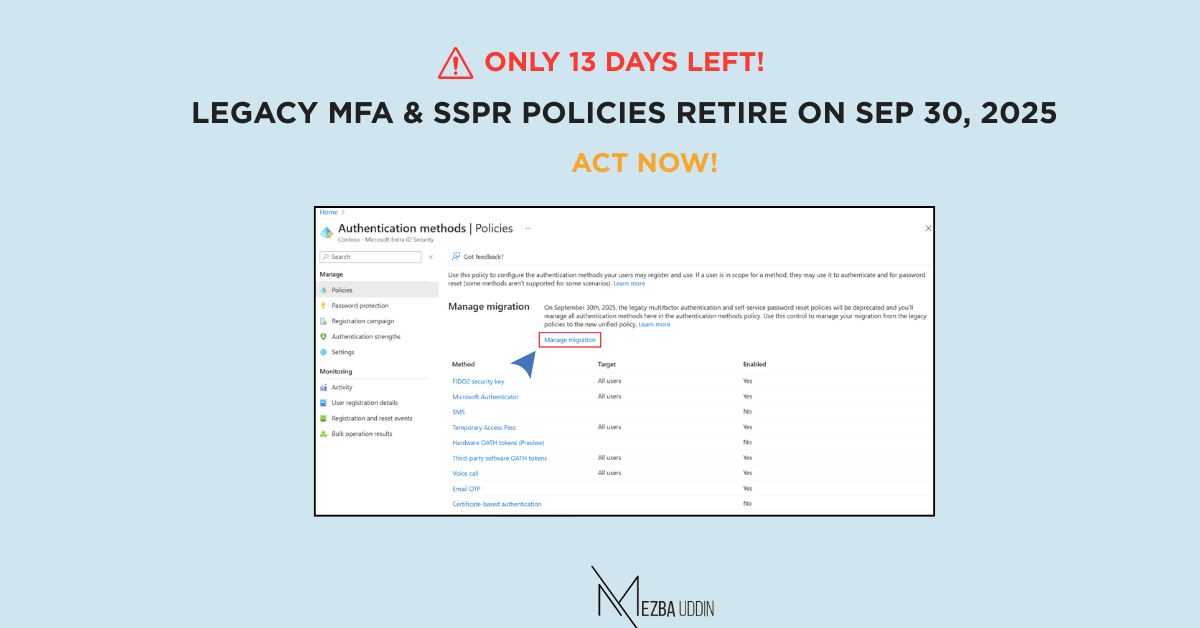
- Authentication methods policy: Entra ID > Authentication methods > Policies
- Legacy MFA tenant settings: Entra ID > Users > Per-user MFA > Service settings
- Legacy SSPR authentication methods: Entra ID > Users > Password reset > Authentication methods
- SSPR security questions: Entra ID > Users > Password reset > Properties
How Migrate MFA and SSPR Policy Settings?
There are two ways in which you can migrate MFA and SSPR policies.
1. Automated migration using the wizard
The simplest way to migrate is through the migration guide provided in the Entra admin center.
-
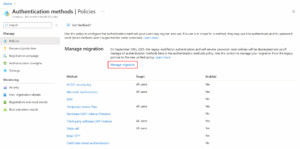
Sign in to the Entra admin center and go to Authentication methods > Policies.
-
Launch Manage migration.
-
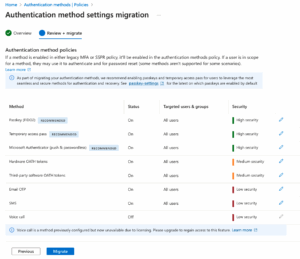
The wizard audits your tenant’s current MFA and SSPR settings and recommends equivalent Authentication methods policy settings.
-
If a method is enabled in either MFA or SSPR, it is recommended to enable it in Authentication methods.
-
-
Review the suggested settings for each method and adjust them using the pencil icon if needed.
-
Select Migrate and confirm. The Authentication methods policy is updated and the legacy policies are grayed out.
-
When you are satisfied with the setup, change the status to Migration Complete.
Key points for the wizard
- The wizard migrates tenant policy settings only. Individual user registrations are not migrated.
- It highlights modern methods like passkeys, Temporary Access Pass, and Microsoft Authenticator passwordless. You should enable these to improve security.
- The migration is reversible until you mark it as complete.
2. Manual migration for more control
If you prefer a slower and more precise approach, you can migrate manually.
1. Audit existing settings
- Export or screenshot settings from the legacy MFA policy, the SSPR policy, and any existing Authentication methods policy configuration.
- Record the scope of users or groups in SSPR.
- Note configuration details such as whether voice calls allow both office and mobile numbers.
2. Start migration in Authentication methods
- Go to Authentication methods > Policies.
- Select Manage migration and set the status to Migration in progress.
- Recreate each authentication method based on your audit. Where MFA and SSPR differ, decide if the method should be enabled for both sign-in and password reset.
3. Test
- Enable methods for a pilot group and test sign-in and password reset.
- Make sure registration and recovery flows still work.
4. Finalize
- Remove methods from legacy policies one by one as you validate them.
- When ready, set the status to Migration Complete so the Authentication methods policy is the only active policy.
Mapping legacy methods to Authentication methods
Use this mapping when migrating.
Legacy MFA → Authentication methods
- Call to phone → Voice calls
- Text message → SMS
- Mobile app notification → Microsoft Authenticator push
- Verification code from app or token → Microsoft Authenticator OTP, third-party OATH apps, or hardware OATH tokens
Legacy SSPR → Authentication methods
- Mobile app notification → Microsoft Authenticator push
- Mobile app code → Microsoft Authenticator OTP
- Software OATH tokens → Third-party OATH tokens
- Email → Email one-time passcode (Email OTP)
- Mobile phone → SMS and Voice calls (mobile)
- Office phone → Voice calls (office phone)
- Security questions → Remain in legacy SSPR
Migration checklist
Below is the migration checklist you can follow.
-
Assign an Authentication Policy Administrator.
-
Audit legacy MFA and SSPR settings.
-
Choose automated wizard or manual migration.
-
Set migration status to In progress.
-
Configure Authentication methods policy for each method.
-
Test sign-in and password reset with a pilot group.
-
Remove legacy methods once validated.
-
Set migration status to Complete.
-
Communicate with users about re-registering methods if necessary.
If you are still relying on the legacy MFA and SSPR policies, begin the migration today. Use the automated wizard for speed, or take the manual route for precision. Either way, make sure your Authentication methods policy is configured, tested, and ready before the retirement date.