If you spend a fair amount of time navigating Microsoft 365 like I do, here’s an important update you’ll want to know about early in 2026. For organizations using Outlook on the web (OWA), one of its longtime security features is retiring—and it comes with a replacement you’ll need to set up.
Microsoft is retiring the old Activity-Based Timeout (ABT) for Outlook on the web.
This feature used to automatically sign users out after a period of inactivity. Once it’s gone, users will no longer be signed out automatically, something that might seem convenient at first (no more unexpected mid-email logouts) but can actually create a security gap if left unaddressed.
Why Microsoft Is Retiring Outlook Web’s Activity-Based Timeout
The main pain point with the old Activity-Based Timeout (ABT) was that it only applied to Outlook on the web. Other Microsoft 365 apps, like SharePoint and OneDrive, had their own separate timeout settings, which made it confusing for admins to manage and inconsistent for users.
To solve this, Microsoft is retiring ABT and encouraging organizations to adopt the Microsoft 365 Idle Session Timeout.
Unlike ABT, this feature works across all supported Microsoft 365 web apps, providing a single, unified control for inactivity timeouts. The idea is simple but powerful: a single, unified dial that controls inactivity timeouts across Microsoft 365. Instead of switching multiple timeout rules for different apps, you now have one policy that applies across Outlook, OneDrive, SharePoint, Microsoft 365 web apps (Word, Excel, PowerPoint), and even the Microsoft 365 Admin Center.
This centralization not only simplifies session management but also strengthens security by making policies consistent and easier to enforce.
Microsoft 365 Idle Session Timeout – The Smarter Way to Manage Inactive Sessions
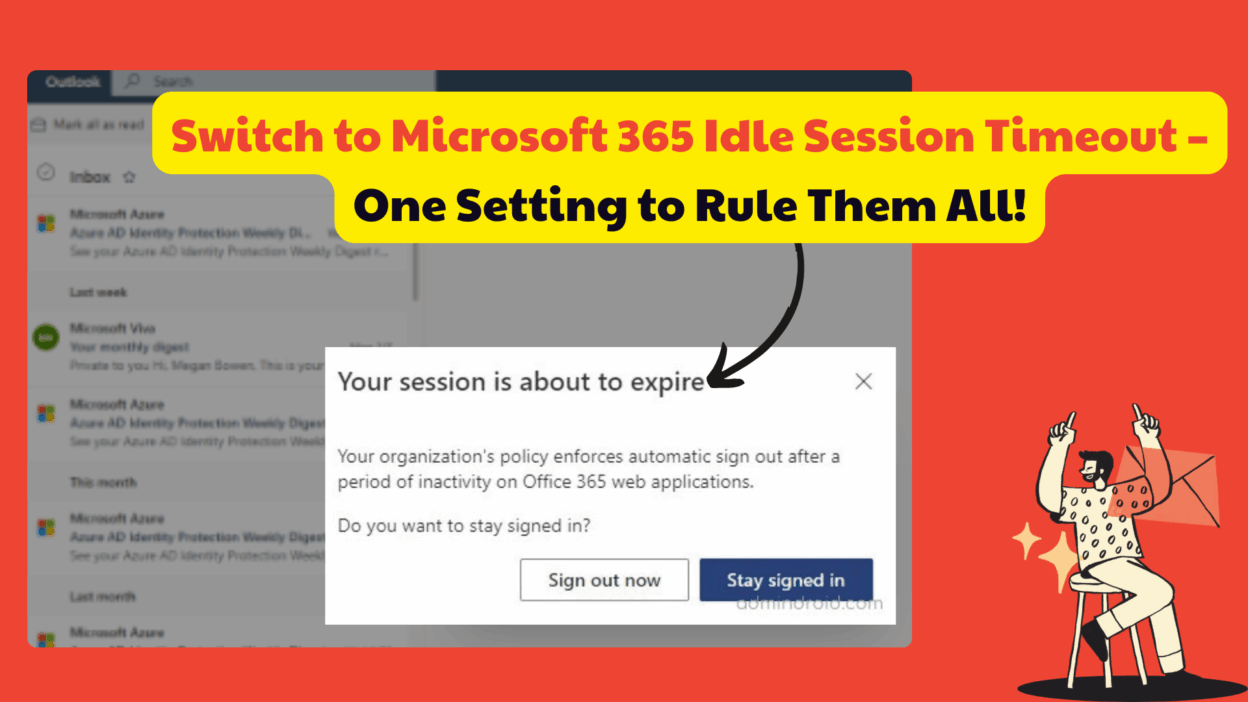
The Microsoft 365 idle session timeout is the crucial replacement you need to enable. If you don’t enable it, your users won’t be automatically signed out of Outlook on the web (or any other Microsoft 365 web app) due to inactivity once the old ABT retires! That’s a potential security gap you definitely want to avoid, especially for users accessing sensitive data from shared or unmanaged devices.
The ‘Microsoft 365 idle session timeout’ is a feature that lets admins set a policy for how long a user can stay inactive before being signed out of Microsoft 365 web apps.
- When the timeout threshold is reached, the user gets a friendly pop-up asking if they want to stay signed in.
- If they ignore it, they get automatically signed out of all supported web apps, Outlook, SharePoint, OneDrive, Microsoft 365 portal, Office web apps, and even admin portals.
One major benefit is that this applies only to web apps—desktop and mobile apps aren’t affected—so your users can keep working uninterrupted on their laptops or phones while still keeping web sessions secure. It’s a clean, web-focused solution that balances security with usability.
How to Configure Microsoft 365 Idle Session Timeout
Setting up an idle session timeout in Microsoft 365 is very easy, but you need the right permissions. You must be a Global Admin for initial activation, while Security Admin, Application Admin, or Cloud Application Admin roles can modify or deactivate the timeout afterward. Here’s a quick step-by-step guide:
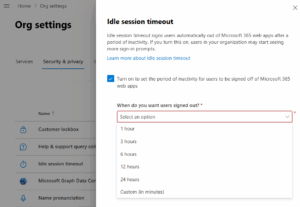
- Go to the Microsoft 365 Admin Center.
- Navigate to Settings → Org Settings → Security & Privacy → Idle Session Timeout.
- Toggle the feature on. You can either use the default time or set a custom duration.
- Save and wait a few minutes for the policy to apply across your organization.
Pro Tip – Go Granular (Optional but Recommended) – Want stricter timeouts for unmanaged devices only? You can do this using an eligible Microsoft Entra ID P1 or P2 subscription. Simply set up a Conditional Access policy in the Microsoft Entra admin center with the “Use app enforced restrictions” session control. This is a great best practice, especially in hybrid work environments. ( I will write about this in detail later)
A few things to keep in mind:
- The timeout applies organization-wide, so you can’t directly scope it to specific users or groups. For granular control, use Microsoft Entra Conditional Access policies.
- It works per browser session, so activity in Edge won’t count as activity in Chrome, and vice versa.
- Users on managed devices or using single sign-on (SSO) may not trigger the timeout, which is expected behavior.
This setup gives you centralized, web-focused control over inactive sessions while allowing flexibility for hybrid or BYOD scenarios.
Why is this better than the old Activity-based Timeouts?
The Microsoft 365 Idle Session Timeout takes everything ABT did and makes it smarter.
- Works across multiple Microsoft 365 web apps, not just Outlook.
- The timeout prompt gives users a chance to stay signed in, reducing frustration from abrupt sign-outs.
- Offers options to apply the timeout only to unmanaged devices, which is perfect for BYOD environments.
- Microsoft plans to deprecate the older Outlook web and SharePoint-specific policies, so moving now avoids last-minute scrambles later.
Basically, it’s more consistent, more secure, and less confusing for admins and users alike.
With Microsoft set to retire older app-specific timeout settings soon, moving to the unified idle session timeout now saves you from last-minute changes later. It’s more secure, more consistent, and far easier to manage, a win for both admins and users alike!