Security policies can be deceptively tricky. You configure them once, feel confident, and months later discover that a single overlooked setting has been quietly leaving your organization exposed.
But what if I told you there’s a brilliant tool within the Microsoft 365 Defender portal that can simplify this daunting task and genuinely elevate your security posture?
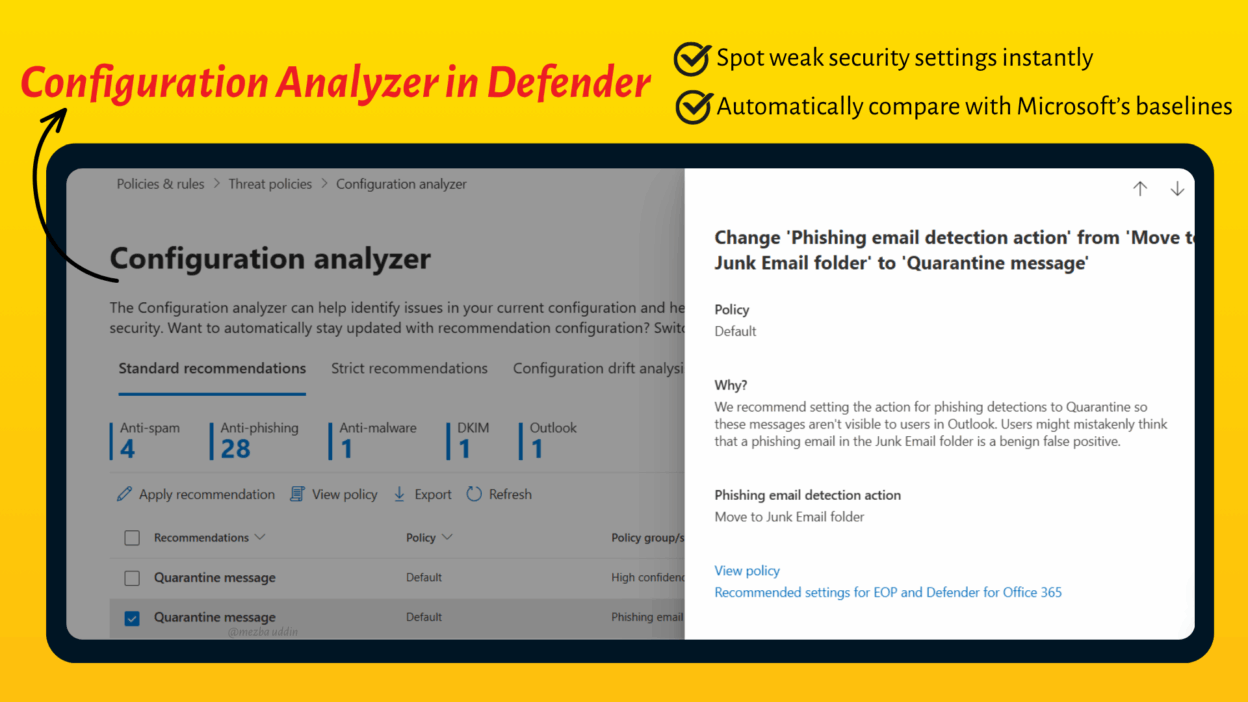
This tool scans your configurations, compares them against Microsoft’s best-practice baselines, and recommends precise fixes to ensure your policies are as robust as they can be.
It’s refreshingly straightforward: Here’s what’s wrong. Here’s how to fix it. I will walk through this capability completely now.
What is the Configuration Analyzer in Microsoft 365 Defender?
In simple terms, it’s a built-in, powerful tool inside the Microsoft 365 Defender portal that compares your current security policy settings against Microsoft’s recommended security baselines.
It takes what used to be a slow, manual review process and automates it, flagging any setting that falls short of best-practice security. Even better, it gives you clear, actionable steps to bring those settings up to standard.
These baselines come in two types: Standard protection and Strict protection. Once it runs the comparison, it shows you:
- Where your settings don’t match the baseline
- Whether you’re falling short of Standard or Strict security levels
- Direct “Apply Recommendation” buttons so you can fix issues instantly
It works like a side-by-side report card for your policies, what you have now vs. what Microsoft thinks you should have.
Standard vs. Strict Recommendations – What’s the Difference?
One of the analyzer’s best features is its ability to offer recommendations based on two distinct security baselines:
Standard Recommendations
- Around 18 recommendations based on Microsoft’s Standard protection profile.
- Ideal for most organizations that want good security while keeping productivity flowing and without being overly restrictive.
- Great for balancing user experience with security needs.
Strict Recommendations
- Around 21 recommendations.
- Designed for organizations with high security needs like finance, healthcare, legal, or government.
- This profile offers a more aggressive, tighter security posture, often with fewer false positives but potentially more aggressive filtering.
- May introduce more prompts or blocks that some users find restrictive, but it’s worth it for the protection level.
Choosing between Standard and Strict really boils down to your organization’s risk tolerance and compliance needs. The analyzer makes it easy to identify the gap between your current settings and these robust baselines.
Policies and Settings it Checks
The Configuration Analyzer isn’t just looking at a couple of things; it’s got a pretty comprehensive checklist:
Threat Policies:
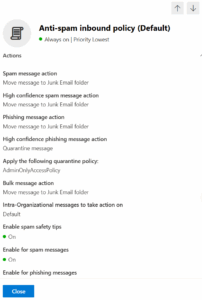
- This includes all the heavy hitters like your Anti-spam, Anti-malware, and Anti-phishing policies.
- For organizations using Microsoft Defender for Office 365, it digs even deeper into advanced anti-phishing settings (like spoof settings, impersonation protection, and phishing email thresholds), Safe Links policies, and Safe Attachments policies.
Non-Policy Settings:
- It goes beyond just policies to check critical configurations like whether you have SPF and DKIM records in your DNS for specified domains (essential for email authentication and preventing spoofing).
- It also verifies if native Outlook external sender identifiers are enabled, which helps users spot emails from outside your organization.
This comprehensive coverage gives a holistic view of your security configuration, not just a partial one.
How to Find the Configuration Analyzer
Users with roles such as Global Administrator, Security Administrator, Global Reader, or Security Reader have the necessary permissions to access the Configuration Analyzer and other Microsoft 365 features. Those in the View-Only Organization Management role group get read-only access, allowing them to review analyzer results without making changes.
- Sign in to the Microsoft 365 Defender portal.
- In the left-hand menu, expand Email & collaboration.
- Click on Policies & rules → Threat policies → Configuration analyzer.
You’ll see tabs for Standard and Strict recommendations, plus a configuration history.
How to Use the Configuration Analyzer
Step 1: Choose Your Baseline – Standard or Strict?
At the very top of the Configuration Analyzer page, you’ll see two prominent tabs:
- Decide if you want to check against Standard or Strict. Standard recommendations will be your default view. If you’re just starting out, I recommend running both. That way, you can see where you stand in both categories.
Reality Check: Most organizations start with “Standard” and then, once those are addressed, evaluate if “Strict” is necessary.
Step 2 – Review the Recommendations
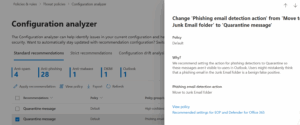
Below your chosen tab, you’ll see a list of policy change recommendations. Each entry represents a setting where your current configuration differs from the selected baseline. You’ll see recommendations like:
- Turn on Safe Attachments for all recipients
- Enable Anti-Phishing policies for all domains
- Configure outbound spam filtering to block specific patterns
When you click on a recommendation, you’ll see your current configuration and the Recommended Value Microsoft suggests based on your chosen baseline (Standard or Strict).
Pro Tip: Don’t apply recommendations blindly. Expand each one to see the details and linked docs, it’s the best way to understand the why behind the change.
Step 3: Taking Action – Apply or View?
Once you’ve reviewed a recommendation and understand it, you have a couple of options:
1. Apply recommendation: For many straightforward fixes, you’ll see an “Apply recommendation” button. Click it to automatically update the policy to the recommended value, usually with a confirmation prompt.
- When to use this: When you’re confident about the change and it aligns with your security goals. It’s great for common, well-understood settings.
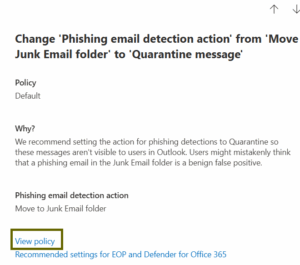
2. View policy: If you want to review or manually edit the full policy before changing it, select the recommendation and click “View policy.” This will open a new tab and take you directly to the specific policy in question within the Defender portal. From there, you can review all its settings and manually make the recommended adjustment (or any other adjustments you deem necessary).
3. This will open a new tab and take you directly to the specific policy in question within the Defender portal. From there, you can review all its settings and manually make the recommended adjustment (or any other adjustments you deem necessary).
- When to use: Choose this when you want full control, need to review the policy before changing it, or when “Apply recommendation” isn’t available.
Step 4: After applying changes, re-run the analyzer to confirm everything matches the baseline.
Configuration Drift Analysis and History
One of my favorite hidden gems in the Configuration Analyzer is its Configuration Drift Analysis and History feature. It’s separate from the “Standard” and “Strict” recommendations, usually located as another tab or section at the top of the Configuration Analyzer page.
This Configuration drift history log shows you how your policies have changed over time and where they’ve started drifting away from the recommended baselines.
- Select a Timeframe: You can typically choose a date range (e.g., last 7 days, 30 days, or a custom range) to see policy changes within that period.
- Review changes: See when and by whom the change was made, the setting name, policy type, old vs. new value, and whether it improved or weakened security compared to the recommended settings. In the history view, you’ll see a timeline of when each deviation occurred and exactly what changed — whether it’s a spam filter tweak, a Safe Links adjustment, or an impersonation protection toggle. With this analyzer, you can easily:
- Spot silent changes – Catch tweaks made quietly by admins or during migrations.
- Track trends – You can see if your environment is gradually loosening up over the months..
- Prove stability – Show consistent alignment with baselines for audits and compliance.
💡 Pro tip: I recommend checking drift history after big projects, new policy rollouts, or admin team changes. It’s the quickest way to make sure nothing slipped out of alignment.
At any point, if you want to keep a record of the recommendations or historical changes, you can export them as a CSV file for reporting, sharing, or maintaining an offline record.
Good Things About Using the Analyzer Effectively
I’ve walked you through what the Configuration Analyzer is and how to use it, but it’s worth pausing to appreciate the real benefits you unlock when you make this tool a regular part of your security routine.
- It’s Built-in: No need for third-party tools or manual checks.
- Proactive, not reactive: This, for me, is the biggest win. Instead of waiting for an incident to occur, the Analyzer helps you identify potential weaknesses before they’re exploited.
- Simplicity in a complex world: Microsoft 365 security policies can be complex, with countless settings, nested options, and interdependencies. The Analyzer cuts through this by giving clear, actionable recommendations, boiling advanced concepts down into simple “do this” steps.
- It’s action-oriented: It doesn’t just tell you what’s wrong, but shows you exactly how to fix it.
- Always updated: Microsoft’s baselines reflect the latest threat trends.
- It saves time: Automates tedious reviews, turning hours of work into minutes and freeing you up for other critical tasks.
The Microsoft 365 Defender Configuration Analyzer is one of those tools you might ignore at first, until you try it and see just how much stronger and safer your environment can be.
Start with the Standard recommendations, get those applied, and then consider the Strict recommendations if your organizational needs demand it. And whatever you do, don’t skip the configuration drift analysis; it’s a goldmine for spotting subtle changes and keeping your security posture rock solid.