Logs are the first place we run to when something looks suspicious. But traditional logs often leave gaps. You see a few details here and there, but the full picture is missing.
- Who really signed in?
- Was it a real user, an app, or one of those new agents?
- What resources were touched?
- Which tenant owns what?
These aren’t just “extra details” anymore; they’re the kind of answers that make or break modern identity security. And the good news is, Microsoft Entra is finally stepping up with the visibility we’ve been asking for.
Microsoft has rolled out some exciting updates to Entra’s logging capabilities. And these aren’t just surface-level tweaks; they’re meaningful improvements that help us get closer to answering the security questions we wrestle with every day.
TLDR:
- With Entra Agent ID, you can finally see agent activity clearly.
- You get transparency into service-to-service sign-ins with the new MicrosoftServicePrincipalSignInLogs stream.
- On top of that, new attributes like SessionID, TenantID, UserAgent, and ASN bring the extra context we’ve all been missing.
Put together, these updates make Microsoft Entra sign-in logs sharper, more useful, and way more actionable. Microsoft is doubling down on transparency, and the logging story will only get better from here.
So next time you dive into your logs, you might actually walk away feeling… dare I say… empowered?
-
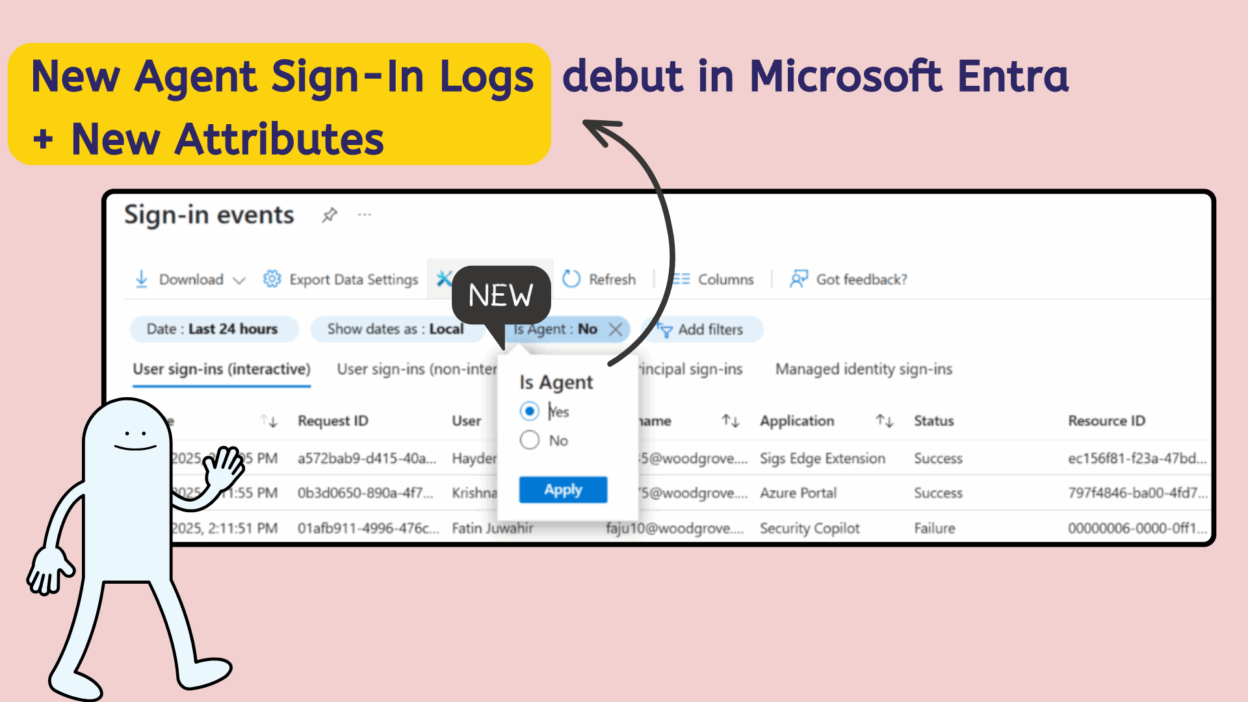
Microsoft Entra Provides Agent Sign-In Logs
One of the biggest challenges today isn’t just tracking user activity; it’s monitoring AI Agents and automated identities.
Microsoft introduced something called Entra Agent ID. It is a way to unify and manage all those agent identities created across platforms like Microsoft Copilot Studio and Azure AI Foundry. Over the next six months, it’s going to expand even further, covering Microsoft Security Copilot, Microsoft 365 Copilot, and even third-party agents.
The reality is that not every sign-in in your tenant is human anymore. With AI-powered assistants and agents becoming mainstream, we now have “non-human identities” that access resources just like users do.
That raises the question: Okay, how do you know what these agents are actually doing? How do you separate user activity from agent activity?
Microsoft Entra now makes this clear with two key announcements:
- agentSignIn resource in MSGraph API → pull out agent-specific data programmatically.
- “is Agent” UX filter in sign-in logs → makes it easy to filter logs and view only agent activity.
-
Introducing Microsoft Service Principal Sign-In Logs
Here’s another headache you’ve probably run into: Microsoft apps interactions between Microsoft services.
For example, you open a Word document inside Teams. To make that work, Teams has to authenticate with Word on your behalf. These kinds of interactions happen all the time between Microsoft services, but until now, they barely showed up in your logs. And even though these aren’t user-driven sign-ins, they’re still token requests happening in your tenant.
To close that visibility gap, Microsoft has introduced ServicePrincipalSignInLogs, now rolling out in Public Preview.
This log stream records token requests whenever Microsoft services authenticate with each other inside your tenant. In short, it records token requests every time Microsoft apps authenticate with each other in your tenant.
Now, before you panic, no, you don’t need to secure these sign-ins yourself. Microsoft already secures them. But having the visibility is priceless.
New Attributes in Entra Sign-In Logs
Let’s get into the details: the attributes. These are the nuts and bolts that turn sign-in logs from plain records into something admins can actually use to answer real-world security questions. Microsoft has added several new attributes designed to give you clearer visibility and better context. Here’s what’s new:
- AppOwnerTenantId
Identifies the tenant that owns the application involved in the sign-in.
- Crucial for cross-tenant scenarios, like when apps from one org access resources in another.
- Helps you see exactly where external apps connecting to your tenant are coming from.
- ResourceOwnerTenantId
Shows the tenant that owns the resource being accessed.
- Complements AppOwnerTenantId; it’s the other side of the coin.
- Perfect for tracking cross-tenant activity in B2B or partner collaboration setups.
- SessionID
Provides a unique identifier for each user sign-in session.
- This makes it way easier to link activity across multiple log streams. Supports broader efforts to add linkable identifiers across Microsoft logging streams.
- Makes it easier to connect the dots during an investigation.
- SourceAppClientID
Lets you trace suspicious activity back to the original source app.
- Detects and investigates impersonation attempts involving federated identity credentials.
- Especially valuable for spotting supply chain–style attacks.
- Entra TenantID in Log Analytics
Now every log entry in Log Analytics includes the originating Entra TenantID in all sign-in and audit Log Analytics schemas.
- For those of you managing multiple tenants (bless your souls), this is gold. Super helpful for organizations managing multiple tenants.
- Simplifies correlation of activity across tenants.
- UserAgent in Service Principal Sign-In Logs
Adds the familiar UserAgent string to service principal sign-ins.
- Gives you another layer of detail, just like with user sign-ins.
- Useful for tracking and flagging suspicious patterns tied to automated identities.
- Autonomous System Number (ASN) in Service Principal Sign-Ins
This one’s geeky but powerful! The ASN attribute gives you insight into the internet origin of traffic.
- Security teams can use this to spot connections from known malicious ranges and build custom rules to block them.
- Adds geo-network-level context to sign-in activity.
👉 Put together, these attributes take sign-in logs from being simple activity records to becoming rich, investigative datasets.
How to Get Started with Microsoft Entra’s New Logging Features
- Check your logging streams: Make sure you’re collecting the latest MicrosoftServicePrincipalSignInLogs if you want full visibility into service-to-service interactions.
- Update your monitoring tools: If you use SIEM or SOAR solutions, integrate the new attributes to create richer correlation rules and smarter alerts.
- Use the Graph API: Use the agentSignIn resource to build custom dashboards that track agent activity in your environment.
- Correlate across tenants: The new TenantID attribute in Log Analytics makes it much easier to connect activity if you manage multiple tenants.
Following these steps will help you start turning all the new logging enhancements into actionable insights without getting overwhelmed.
How Entra Sign-In Log Improvements Improve Security Visibility and Investigations
I know, I know, reading about new log attributes doesn’t exactly make your heart race. But these updates have a very real impact on your daily security and IT operations:
- Better threat detection: Attributes like SourceAppClientID and ASN data make it easier to flag impersonation attempts or malicious traffic that used to fly under the radar.
- Faster investigations: With unique identifiers like SessionID, you can follow an event across multiple log streams without piecing things together manually.
- Simpler compliance reporting: Cross-tenant details (AppOwnerTenantId, ResourceOwnerTenantId) help demonstrate control in multi-tenant and complex environments.
- Clearer operational insights: Being able to separate users, agents, service principals, and Microsoft services reduces confusion and keeps investigations focused.
In short, these aren’t just cosmetic changes; these details can save hours (sometimes days) of your investigation and reporting workflows.
Clearer Visibility Means Stronger Security
It’s also obvious that Microsoft has been listening. For years, admins have asked for more clarity, actionable details, and real insight from logs—and these enhancements deliver exactly that.
At the end of the day, logs are only as useful as the insights you can extract from them. And with these new updates, Microsoft Entra is making sure we’re not just collecting data; we’re empowered to act on it.