Azure Monitor Logs is an essential pillar for organizations seeking unified, scalable observability across their cloud environments. While centralized logging offers consistency, security-conscious teams often need precise access controls—down to the individual data row. With the public preview of Granular Role-Based Access Control (RBAC), Azure Monitor Log Analytics takes fine-grained access control to the next level.
This capability brings attribute-based access control (ABAC) into Azure Monitor, empowering you to enforce least privilege access across users and teams based on data properties, without having to split logs across multiple workspaces.
What is Granular RBAC?
Granular RBAC enhances Azure’s existing access mechanisms by introducing the ability to limit access at both the table and row level in a single Log Analytics workspace. It uses ABAC conditions as part of your Azure RBAC role assignments, allowing you to control what data each user can see or query based on metadata or content-level attributes. To configure Granular RBAC in Azure Monitor Logs, certain permissions are required.
- Creating a custom role requires the Microsoft.Authorization/roleDefinitions/write permission.
- To add or modify conditions, you’ll need both Microsoft.Authorization/roleAssignments/write and Microsoft.Authorization/roleAssignments/delete permissions at the workspace level.
- These permissions are typically included in privileged built-in roles such as User Access Administrator and RBAC Administrator.
Why Use Granular RBAC?
Granular RBAC addresses critical enterprise needs:
- Data Segregation: Enforce access based on business unit, geography, device type, or any custom identifier.
- Data Privacy: Shield sensitive data like personal identifiers, financial records, or healthcare info.
- Regulatory Compliance: Align access control with legal and industry-specific mandates without duplicating log storage.
How to Configure Granular RBAC in Azure Monitor?
1. Define a Custom Role
Your custom role must specify the following permissions:
| Scope | Action | Description |
|---|---|---|
| Control plane | Microsoft.OperationalInsights/workspaces/query/read |
Run queries and view metadata |
| Data plane | Microsoft.OperationalInsights/workspaces/tables/data/read |
Enables access to actual data |
| Optional | Microsoft.OperationalInsights/workspaces/read |
Portal visibility |
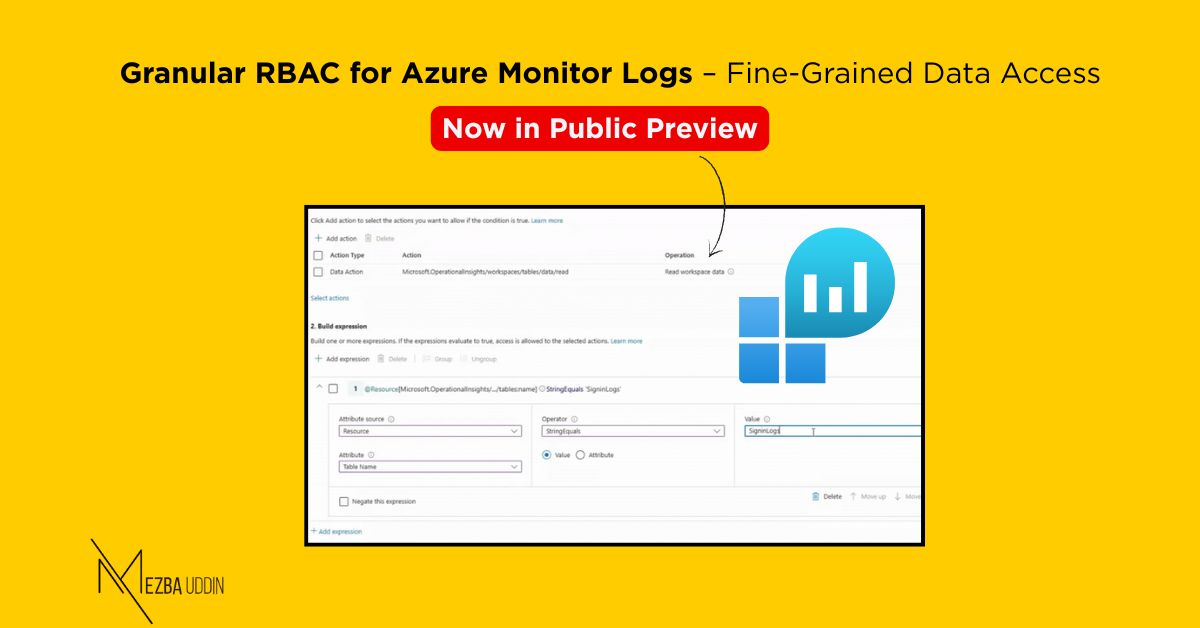
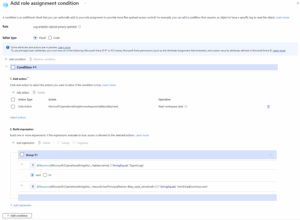
2. Create Role Assignment with Conditions
- Navigate to Azure Role Assignments
- Select Add condition
- Under Add action, choose
Read workspace data - Build an expression using:
-
Table Name(to specify which table) -
Column Value(to filter based on data content)
-
Conditions are expressed in the format: Attribute Operator Value
Examples:
- Allow access only to logs from
Region = WestUS - Deny visibility into records where
userPrincipalName = CEO@example.com
3. Expression Logic and Operators
Granular RBAC supports ABAC operators optimized for string matching:
| Operator | Description | KQL Equivalent |
|---|---|---|
StringEquals / StringEqualsIgnoreCase |
Exact match (case-sensitive/insensitive) | == / =~ |
StringNotEquals / StringNotEqualsIgnoreCase |
Inverse match | != / !~ |
StringLike / StringLikeIgnoreCase |
Partial match | has_cs / has |
StartsWith / StartsWithIgnoreCase |
Begins with | startswith_cs / startswith |
ForAllOfAnyValues:StringEquals |
Similar to in() |
N/A |
ForAllOfAllValues:StringNotEquals |
Similar to !in() |
N/A |
Tip: Use data transformation rules to clean or normalize data (e.g., standardize casing or group high-cardinality values like IPs into subnet categories).
4. Set Conditions
- Ensure the role’s assignment scope matches the conditions—e.g., don’t assign at a subscription level if your expression filters a specific table.
- Remove broader permissions like
*/readfrom the same scope, or they will override granular rules. Azure RBAC follows an additive model—the most permissive rule applies.
Points to Remember:
- Granular RBAC is supported only in the public cloud.
- Data export does not enforce granular access conditions.
- Only workspace-based Application Insights are compatible.
- Search Jobs and Summary Rules may fail without full table access.
- In Microsoft Sentinel, ABAC conditions don’t apply to replicated data like bookmarks or incidents.
- Use LAQueryLogs and Azure Activity Logs for auditing user actions.
- If Access Control Mode is set to “Use resource or workspace permissions,” ABAC conditions are ignored.
Granular RBAC in Azure Monitor Logs marks a significant step toward fine-tuned data governance—empowering organizations to maintain centralized logging while enforcing precise, secure, and compliant access control at every layer.