Let’s start with a small story we’ve all been part of (knowingly or not).
We all live on multiple devices. We begin a task on the desktop, continue it on the laptop, and wrap it up on the phone during the commute. This cross-device rhythm defines how we work today, and that’s exactly what the Authentication Transfer Flow is built to support.
Convenient? Absolutely.
A win for user experience? No doubt.
Authentication Transfer is designed for this: a seamless, passwordless experience that transfers your authenticated state from one device to another. But what feels effortless for users can quietly open doors you didn’t mean to unlock.
In this blog, I’ll explain this underrated yet powerful feature, and why and when you should block the Authentication Transfer flow using Conditional Access (CA) policies.
The Convenience Trap – What is Authentication Transfer
The Authentication Transfer Flow is a mechanism designed by Microsoft to eliminate sign-in friction when moving an authenticated session from one endpoint to another. The most common use case is shifting a session from a PC or web app to a mobile device.
For users, this is gold. You skip the hassle of signing in again. But for admins, it’s where ease meets exposure.
That same convenience can quietly slip past some of your strongest security controls, like device compliance, app protection policies, or even Conditional Access checks.
Let’s look at how this can backfire:
Say your organization allows Outlook for desktop only on managed corporate devices but restricts Outlook mobile on personal phones.
A user signs into Outlook on their corporate laptop. They see a prompt: Want to use Outlook on your phone? Just scan this QR code.
They scan it using their personal phone, and just like that, they’re signed into Outlook mobile. The mobile device inherited the authenticated session from the desktop, completely skipping Conditional Access revalidation.
Even though your policy explicitly says “block personal devices,” the user is in.
No MFA. No compliance checks. No enforcement!
In short, your security boundary just got bypassed in seconds.
The Problems — What Attack Surface Does This Create?
This isn’t about users breaking rules; it’s about attackers exploiting the same seamlessness that makes Authentication Transfer so convenient.
Here are some attack scenarios to consider:
🕵️ Attack Vector 1: The Rogue Session Replay
In a typical session replay attack, an attacker steals a user’s session token and uses it to impersonate them. The danger with Authentication Transfer Flow is that it legitimizes the transfer of an active session token to a completely new, unverified endpoint.
Now imagine a worst-case scenario: an employee’s corporate PC is quietly infected with infostealer malware. The malware can’t grab the user’s password or bypass MFA, but it can:
- Silently monitor the network for the traffic involved in QR code generation.
- Intercept the unique, temporary token used in the transfer flow.
- Programmatically initiate the transfer to an attacker-controlled endpoint (a virtual phone or a rogue device).
If the attacker intercepts and replays that token before the real user does, they’ve just placed a legitimate corporate session onto their own unmanaged device, no credentials, no MFA, no alarms triggered.
They’ve essentially weaponized convenience itself.
🕵️ Attack Vector 2: The Insider Threat
Insider threats are often the hardest to predict. A disgruntled employee who knows they’re about to leave the company and wants to exfiltrate data before access is revoked.
- They know their corporate laptop is heavily monitored.
- They know attempting to forward emails to their personal address is logged.
- And they know Outlook mobile isn’t allowed on personal devices.
So, what do they do? They use the Authentication Transfer Flow as their loophole. They generate the QR code, scan it with their personal phone, and now, they’ve got a live, synced copy of their corporate mailbox right in their pocket.
From that point on, the corporate security team loses all visibility. The data sits on an unmanaged, unmonitored device, free to be backed up, copied, or synced to personal cloud storage.
A clean, silent exfiltration, all through a legitimate feature.
How Conditional Access Strengthens Controls Over Authentication Transfer
Conditional Access in Microsoft Entra ID is the backbone of modern authentication governance in Microsoft 365. Recognizing that convenience flows like Authentication Transfer and Device Code Flow could unintentionally bypass some security checks, Microsoft introduced a new CA condition called Authentication Flows.
To be very clear, Authentication Transfer wasn’t built to weaken security; it was designed to make sign-ins smoother, especially in passwordless environments. It helps users switch between devices without re-entering credentials, reducing friction and support tickets. But like any powerful capability, it needs boundaries!
To enforce this boundary, Conditional Access puts you in control of the flow. You’re essentially telling Entra ID:
Before transferring a session from Device A to Device B, verify it against policy. If it doesn’t meet the criteria, block the transfer!
This one control makes a big difference. Instead of session tokens hopping freely between devices, Entra ID now validates compliance first, ensuring every transfer follows your organization’s rules.
Admins can explicitly allow or block Authentication Transfer (and Device Code Flow) using Conditional Access.
The Key Difference
Blocking the flow doesn’t block the user from signing in; it just blocks the transfer method.
- If the flow is BLOCKED: When the user scans the QR code, the process fails. The mobile device then has to go through a full, standard sign-in instead.
- The Power of Full Sign-In: A full sign-in request triggers all existing Conditional Access checks, ensuring the device is properly evaluated for:
- Device Compliance: “Are you enrolled in Intune and compliant?” (If not — Access Denied)
This one simple CA policy ensures unmanaged devices can’t slip through using convenience flows. It forces a proper authentication route, restores your intended security posture, and makes sure your data only reaches trusted, compliant devices.
How to Block Authentication Transfer Using Conditional Access Policy
The configuration process is surprisingly simple and will give you a huge confidence boost in your security baseline.
Here’s how to create a Conditional Access policy to block Authentication Transfer:
Step 1: Sign in to the Microsoft Entra admin center with at least Conditional Access Administrator privileges.
Step 2: Go to Conditional Access → Policies → + New policy
Step 3: Give your policy a clear, descriptive name — for example, CA_001_Block_Auth_Transfer_Flow. (Good naming makes life easier later!)
Step 4: Configure Assignments. Under Assignments, set the following:
- Users: Include All users or specific groups who shouldn’t use Authentication Transfer.
- Target resources: Under Resources → Include → choose “All resources” or specific apps (like Outlook, Teams, etc.) you want to restrict. For flows that can affect multiple apps, broader targeting works best.
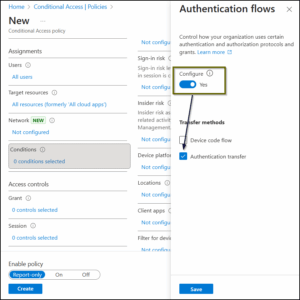
Step 4: Configure the conditions: This is the core of the policy!
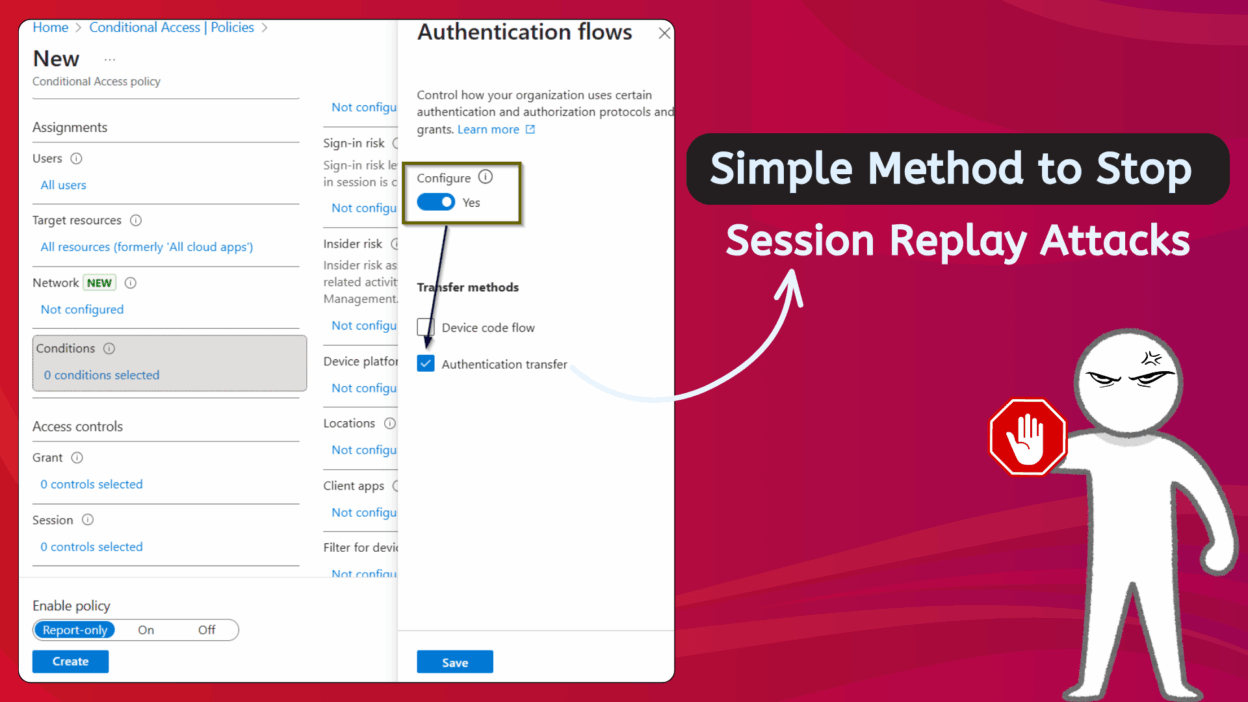
- Under Conditions → Authentication Flows, toggle Configure to Yes.
- You will see two checkboxes: Device Code Flow and Authentication transfer. Select Authentication Transfer.
- Click Done.
(If you also want to block Device Code Flow, check that box too — both can be selected together.)
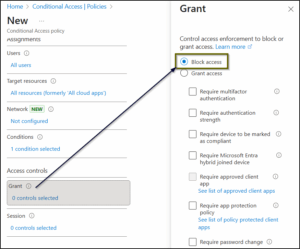
Step 5: Under Access controls → Grant, select Block access → Select. This is the part that enforces the block.
Step 6: Choose either Report-only’ or ‘On’mode.
Pro Tip: Always start with Report-only mode! This allows the policy to evaluate but not enforce. You can then check your sign-in logs for a few days to see who would have been blocked (and why!) before you switch it to On.
Once active, users will no longer be able to transfer authentication sessions between devices. You’ve just shut down a subtle, high-risk bypass and strengthened your Conditional Access framework.
When Should You Block Authentication Transfer?
Here’s a quick reality check: you don’t always have to block it! It really depends on your organization’s access model and risk tolerance.
You should consider blocking Authentication Transfer if:
- You don’t allow personal devices to access Outlook, Teams, or any Microsoft 365 apps.
- You have strict data residency and compliance policies that require managed device access.
- You’re using Intune app protection or mobile application management (MAM) and don’t want unmanaged devices to bypass it.
- You operate in a high-security or regulated industry (finance, defense, healthcare, etc.) where session handoffs are risky.
In other cases, it’s best to start by monitoring. See how often Authentication Transfer occurs and who’s using it before deciding to enforce a block.
Authentication Transfer is not a vulnerability by itself!
But in the wrong setup, it can quietly become an unmonitored bridge between devices that breaks your compliance chain.
As stewards of corporate data, our responsibility is to strike the right balance between convenience and control. For high-security environments, strict BYOD policies, or organizations that can’t risk data landing on unmanaged devices, this flow can introduce a blind spot you can’t afford to overlook.
So, go ahead, implement this, and rest a little easier knowing you’ve plugged yet another hole in your organization!