Think of this hypothetical situation: An employee signs up for a new app, clicks “Allow” to access their Microsoft 365 emails or files, and—poof! Suddenly, that app has permission to read, edit, or even share sensitive company data. Scary, right?
Microsoft 365 has a setting that lets users consent to third-party apps accessing org data. Convenient? Maybe. Safe? Definitely not. In this blog, I’ll show you why you should disable it, what risks it poses, and how to lock it down in just 10 minutes. ✌️
Why Disable User Consent to Apps?
Most employees aren’t cybersecurity experts—they’re focused on work, not scrutinizing app permissions. Allowing user consent means they can grant third-party apps access to company data, and here’s what could go sideways if users can freely grant access:
- Unintentional Data Exposure: Not all apps are created equal. Some might not have adequate security measures, which could lead to your sensitive company data being exposed.
- Phishing Attacks in Disguise: Hackers often create fake apps that look legitimate (think “Microsoft Login Helper” or “PDF Viewer Pro”). If a user grants permissions, attackers gain a backdoor to emails, calendars, or SharePoint. I’ve seen companies lose months of work this way.
- Compliance Violations: GDPR, HIPAA, CCPA—most regulations require strict control over who accesses sensitive data. If an app you’ve never audited starts slurping up customer info, you’re on the hook for fines, not the employee who clicked “Allow.”
- Data Leaks You Can’t Track: Once an app has access, it can export data outside your organization. And if that app gets hacked? You’ll have zero visibility into where your data went or how to shut it down.
What’s the Purpose of This Setting Anyway?
Why does this setting exist if it’s so risky? Well, Microsoft isn’t trying to sabotage you, promise! The user consent feature exists to streamline workflows.
For example, letting a sales team connect their CRM to Outlook without waiting for IT approval. But here’s the problem: convenience ≠ security.
By default, Microsoft 365 allows users to consent to apps requesting low-risk permissions (like reading a profile) and even high-risk ones (like full access to emails). Unless you intervene, your org is one eager employee away from a breach.
What’s the Purpose of Disabling User Consent to Apps?
Disabling user consent is a proactive security measure by ensuring:
- Only Trusted Apps Get Access: IT vets and approves apps before they touch your data.
- Enhanced Security: Reduces the risk of malicious apps sneaking in.
- Regulatory Compliance: Helps meet GDPR, HIPAA, and other standards.
- Better Oversight: IT gains full visibility into app interactions, making risk management easier.
How to Disable User Consent in Microsoft 365
Now, let’s get to the practical part: how to actually disable this setting in Microsoft 365. Don’t worry; it’s simpler than you think. Follow these steps:
- Head to https://entra.microsoft.com and log in with your admin account.
- In the left menu, go to Applications > Enterprise Applications.
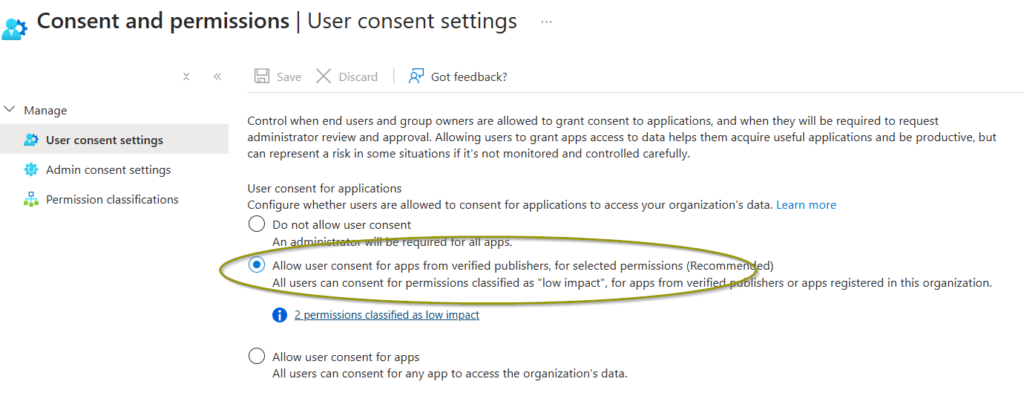
- Under the “Security” section, find User consent settings and click it.
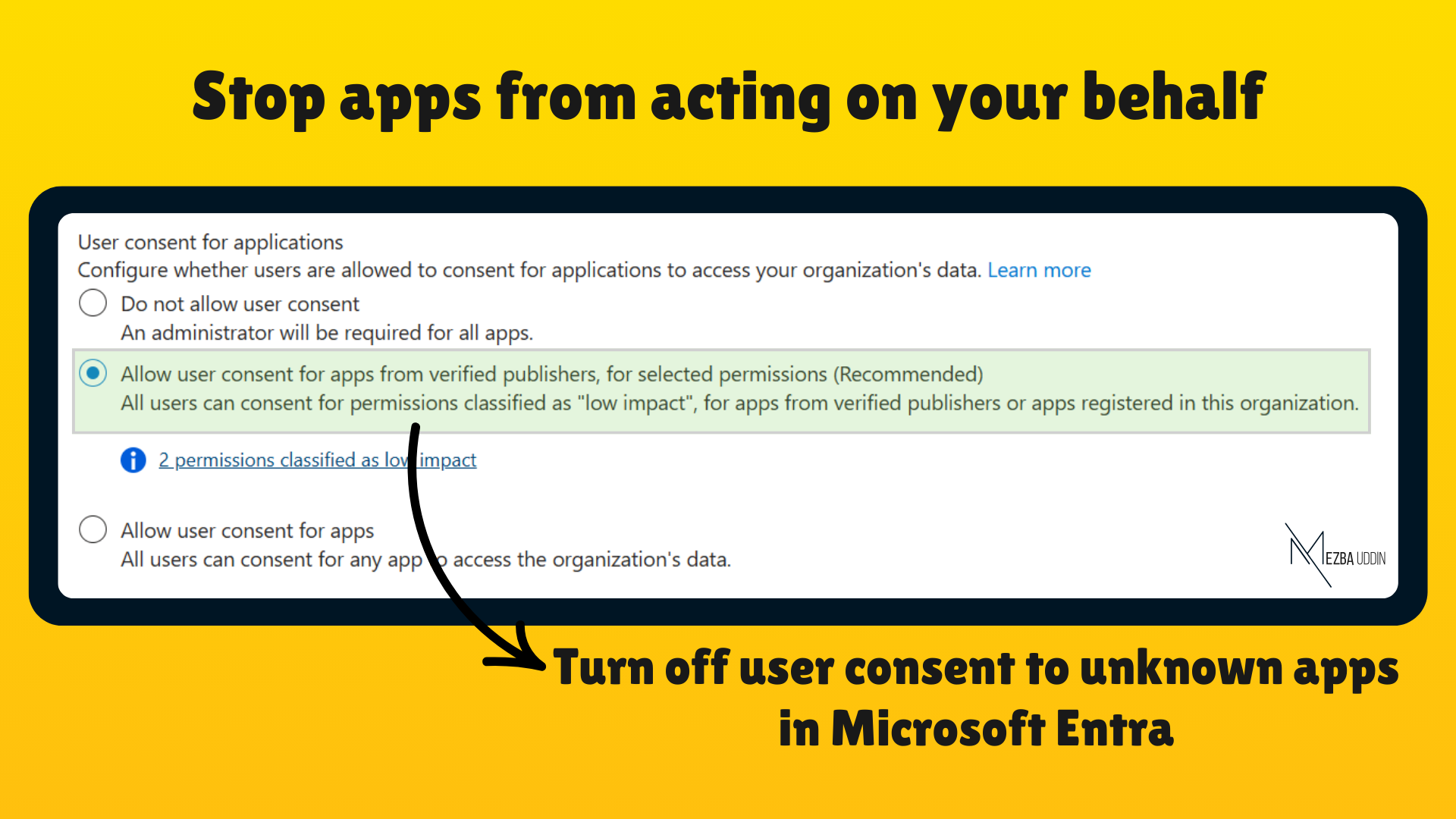
- Your existing option would have been set to 3rd option. Now change the setting from “All users can consent” to “Allow user consent for apps from verified publishers, for selected permissions (Recommended).”
- Then, configure low-impact permissions users can consent to by selecting “Permissions to classify as low impact.”
(Optional) Set up the Admin Consent Workflow to help users request approval for apps requiring admin consent.
- Finally, hit Save and notify your employees about the change and why it matters—it’ll help avoid confusion and get everyone on board!
But Wait—What About Legitimate Apps?
Great question! Disabling user consent doesn’t mean banning apps forever. Instead, IT admins can:
- Pre-approve trusted apps (like Zoom or Slack) for the entire org.
- Set up a process where employees submit app requests for review.
- Use conditional access policies to limit app permissions by department.
This way, productivity stays high, but security stays higher.
Final Thoughts: Don’t Gamble with Your Data
Disabling user consent to apps might seem like a small step, but it’s a powerful one. Sure, it might add a tiny bit of friction for users, but the security benefits far outweigh the inconvenience.
So, take 10 minutes today to tweak those settings. Your future self (and your company’s lawyers) will thank you.
If you have any questions or need help, drop them in the comments below!