As cyber risks grow more sophisticated, IT administrators juggle the dual roles of security enforcers and access facilitators. While access control mechanisms like Conditional Access (CA) have provided some relief, they still suffer from inherent delays when managing user sessions. Specifically, the time between when a user’s account is disabled and when access is revoked can leave room for exploitation.
Continuous Access Evaluation (CAE) addresses this gap by ensuring near-instantaneous session termination following critical changes. This post delves into the technical underpinnings of CAE, exploring its configuration, practical applications, and the advantages it offers to organizations seeking optimal security and user experience.
What is Entra ID Continuous Access Evaluation (CAE)?
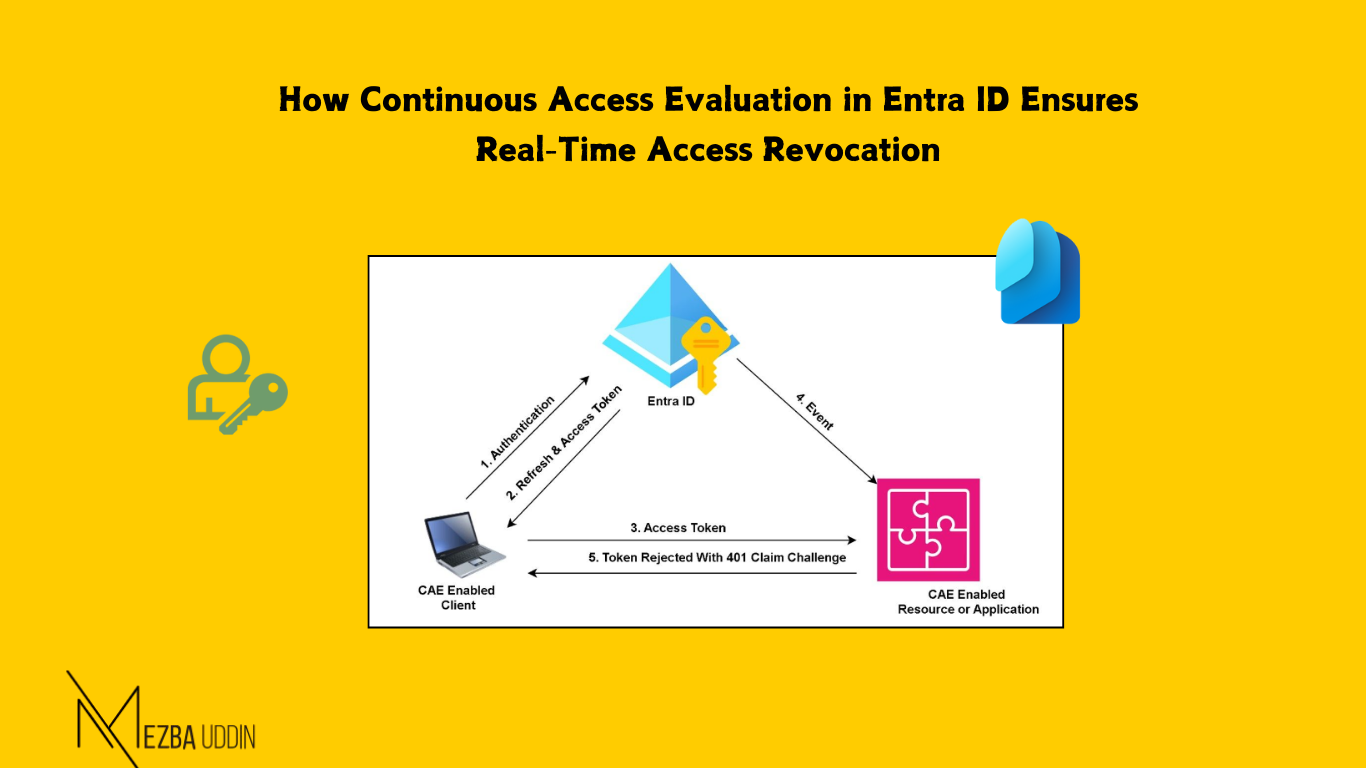
Continuous Access Evaluation (CAE) is a real-time security mechanism within Entra ID that enhances session management by evaluating user access continuously throughout their session. The core principle of CAE lies in its ability to immediately reflect changes in a user’s status (e.g., account disabling, MFA activation) by evaluating access tokens in real-time, which directly challenges the conventional session control model that operates based on token expiry. This feature is enabled by default.
In essence, CAE facilitates a dynamic, bidirectional communication channel between Entra ID (the token issuer) and client applications (the relying parties). By ensuring that critical access changes are enforced without waiting for token expiry, CAE reduces the window of vulnerability that could be exploited by attackers.
License Requirement:
Azure AD Premium P1 or P2 licenses are required for customization and full functionality of CAE.
Key Features of CAE:
- Real-Time Access Management: CAE ensures that any critical event, such as a password reset or account disablement, immediately revokes the user’s session—without delay.
- OAuth Token Handling: In a typical OAuth 2.0 flow, access tokens are cached for 1 hour, and clients rely on the token for session persistence. CAE allows for the invalidation of these tokens, ensuring users lose access to resources the moment a critical change occurs.
- Conditional Access Integration: CAE is integrated with Azure AD’s Conditional Access policies, enhancing security by enforcing real-time policy updates and blocking access without waiting for token expiration.
The Need for Continuous Access Evaluation
Traditional session control mechanisms often suffer from a significant lag between when access should be revoked and when it actually happens. Access tokens in Azure AD typically have a 1-hour lifetime, meaning if a user’s permissions change (e.g., an admin disables their account), it can take up to 60 minutes for the session to be terminated. During this window, the user might still have access to critical resources.
Consider a scenario where an administrator disables a user’s account due to suspicious activity. Without CAE, the user may still have access to confidential resources for the next hour, giving them ample time to exploit the situation. CAE resolves this by immediately invalidating the user’s session, mitigating the risk of data exfiltration or malicious activity.
How CAE Works Under the Hood
At its core, CAE operates through OAuth 2.0 access tokens, which are used to authenticate requests between users and Azure AD-supported apps (e.g., Exchange, SharePoint Online, and Teams).
When a user requests access to a service, they receive an access token, which has a 1-hour expiration. However, this token is not refreshed unless explicitly triggered by a refresh token request. CAE, in contrast, ensures that if a critical event occurs (like account disablement), the access token is instantly invalidated and replaced, halting further access.
- Claim Challenge: A major feature of CAE is the claim challenge, which informs the client app that the cached token is no longer valid, even if it hasn’t expired yet. The client app is forced to request a fresh token from Azure AD, ensuring that the user’s session is terminated immediately.
- Client-Side Support: CAE is supported by various CAE-capable clients including Teams, Exchange, SharePoint, and Outlook (on multiple platforms: web, Win32, iOS, Android, macOS). However, note that Office on the Web is currently not supported.

Critical Events Triggering CAE
CAE’s strength lies in its ability to evaluate critical events in real-time and ensure that access tokens are invalidated immediately. Here are some of the key events that CAE addresses:
- User Account Deletion or Disabling
- Password Reset or Change
- Location or IP Address Change
- Multi-Factor Authentication (MFA) Activation
- Refresh Token Revocation
- High-Risk User Detection via Identity Protection
Conditional Access and Location Enforcement
Additionally, CAE provides another layer of security through location-based checks. When a client attempts access, Entra ID evaluates the Conditional Access Policy for the application or resource, attaching a Conditional Access Policy ID (CAPID) to the Access Token. If the client changes locations, Entra ID ensures that the new location is evaluated, and a mismatch will trigger a 401 challenge. This process ensures that tokens are only valid for the intended locations, preventing unauthorized access from stolen tokens, even when they’re used in different locations.
However, enabling strict location enforcement could potentially disrupt access if network traffic is routed through different IP addresses. Consider this scenario:
- Client1 initiates a request to Exchange Online, and the traffic passes through an IP like 193.20.1.10.
- If the same token is later used from a different IP (e.g., 193.30.1.20), the resource may block access due to the IP mismatch, believing it to be unauthorized.

In conclusion, Continuous Access Evaluation (CAE) is a game-changing feature for Azure AD, transforming session management by enforcing real-time policy enforcement and minimizing access delays. By integrating seamlessly with Conditional Access, CAE enhances security while maintaining a smooth user experience.
As enterprises shift towards modern security paradigms, adopting CAE ensures immediate protection against unauthorized access and data breaches, cementing its role as a critical security measure in the cloud-first world.